As an industry strategist with three decades of experience in drilling, production, processing and logistics systems, I’ve witnessed how deeply software vulnerabilities can cascade through operational chains—from control systems to supply-chain management. With that background, I find the recent launch of Aardvark by OpenAI noteworthy: it represents a meaningful shift in how we think about code security in the development workflow.

In this blog I’ll walk you through how Aardvark works, why it matters (especially for environments where reliability and safety are paramount), the practical implications for engineering organisations, some performance stats, as well as five frequently asked questions. I’ll also share assumptions and caveats—because in complex systems, nothing is ever plug-and-play.
What is Aardvark and how does it work?
Aardvark is described as an autonomous security-researcher agent powered by GPT‑5, built to scan entire code repositories, reason about threats, validate exploitability and propose patches.
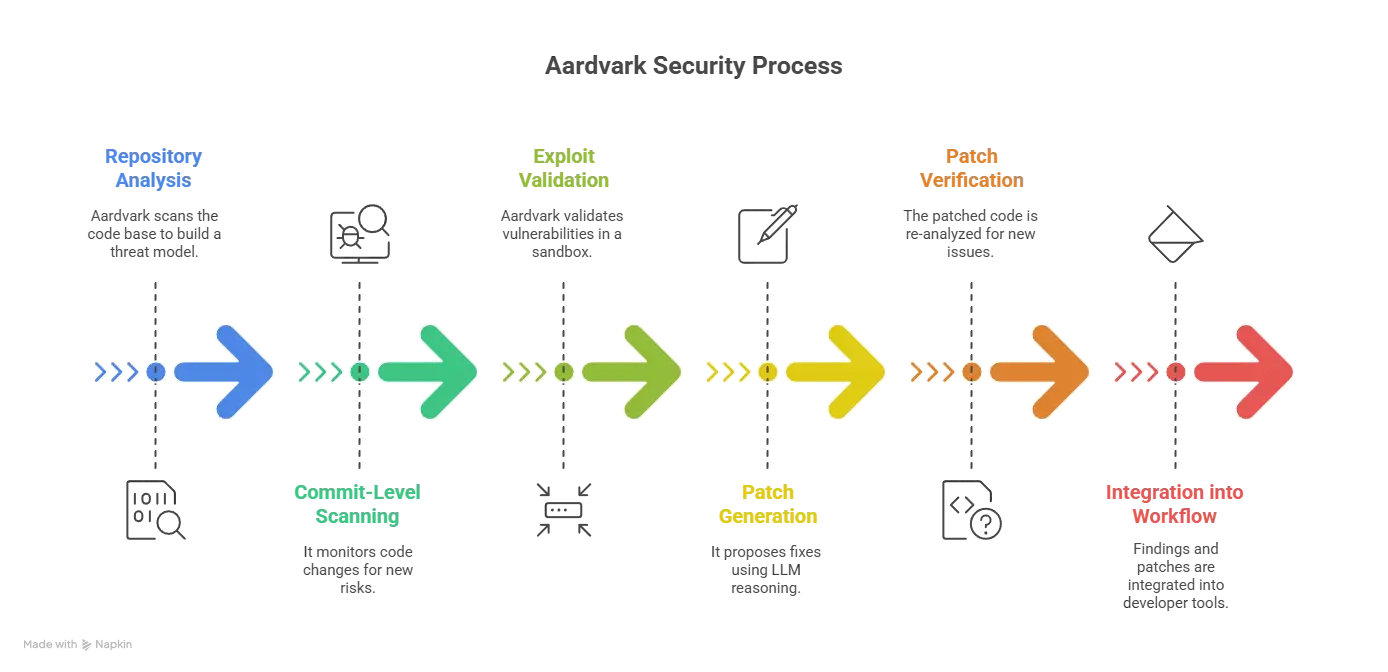
Key functional stages:
-
Repository analysis / threat modelling: Aardvark begins by scanning the full code base (or a large portion) to build a “threat model” of how the system is organised, its functionality and likely risk zones.
-
Commit-level scanning: It monitors incoming code changes (commits) in a continuous integration / continuous deployment (CI/CD) pipeline and checks if any new change introduces risk or violates existing patterns.
-
Exploit validation: Once a candidate vulnerability is flagged, Aardvark attempts to trigger or validate the exploit in a sandboxed environment, to reduce false positives.
-
Patch generation and verification: Using the LLM reasoning plus integration with a code generator (for example, Codex) it proposes a fix, then re-analyses the patched code to ensure no new issue is introduced.
-
Integration into developer workflow: The work is designed to integrate with tools like GitHub so developers receive actionable findings and patches rather than generic alerts.
In short, Aardvark shifts from “scan then alert” to “scan → validate → fix” with reasoning built in.

Why does this matter for engineering and enterprise contexts?
From a strategic / operational viewpoint, the significance is several-fold:
-
Shifting security left: Traditional workflows often treat security as an end-of-cycle activity—after development, before deployment. By embedding a system like Aardvark in the CI/CD pipeline, you move security upstream. That reduces the risk of undetected vulnerabilities traveling into production.
-
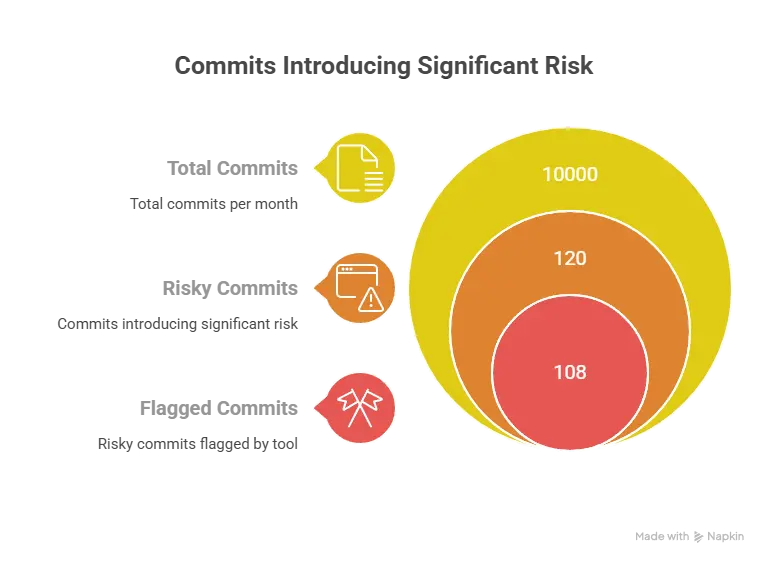
Scale and speed: In large enterprise systems (e.g., complex control systems, logistics platforms, supply-chain software), manual code review and security audit struggle to keep pace. A 1.2 % rate of commits introducing bugs (per OpenAI’s own figures) means even small change sets can accumulate risk.
-
Reducing false positives: One key pain point in existing static analysis / vulnerability scanners is the volume of false alarms, which drains teams and undermines trust. The sandbox-verification stage in Aardvark addresses this.
-
Operational/industrial implications: In operator environments — drilling systems, production monitoring, processing controls, logistics flows — software failures or exploits not only pose cyber risk but also safety, environment and business-continuity risks. A proactive agent that reasons about code behaviour can help mitigate these systemic risks.
-
Supply-chain & open-source risk: Because many systems rely heavily on open-source components and shared libraries, vulnerabilities in those upstream modules propagate widely. Aardvark’s capability to scan repositories (including open-source) and propose patches helps strengthen the ecosystem.
Performance and metrics
Here are some headline figures and practical metrics (based on published data and my interpretation):
-
In benchmark testing on “golden” repositories, Aardvark reportedly identified 92% of known and synthetically introduced vulnerabilities.
-
According to the launch announcement, over 40,000 CVEs were reported in 2024 alone, underscoring the scale of the task.
-
OpenAI reports ~1.2% of commits introduce bugs that can have “outsized consequences”.
-
In open-source trials, Aardvark reportedly discovered 10 officially assigned CVEs.
From an engineering operations lens, these metrics imply: if you run 10,000 commits per month through a pipeline, with an estimated 120 commits introducing significant risk (using the 1.2% figure), then a tool that catches ~90% of those means ~108 risky commits might be flagged and patched early rather than slipping through. That leads to a meaningful reduction in exposure window and downstream remediation cost.

Practical considerations & use-case roadmap
When incorporating a system like Aardvark, here are practical steps and caveats:
Assumptions
-
I assume your codebases are sufficiently mature (e.g., structured, version-controlled, CI/CD pipelines exist) so that the agent can integrate.
-
I assume you have or will establish the human-in-the-loop review process for patches (even though automation is high, human oversight remains vital).
-
I assume the codebase is large and complex enough that manual security review is already a bottleneck (i.e., there is a need for this scale).
Implementation roadmap
-
Pilot on critical repositories
-
Select high-value codebases (production modules, high-risk services) and onboard Aardvark or equivalent.
-
Monitor how many findings are produced, how many false positives, how many suggested patches are adopted.
-
-
Integrate into CI/CD
-
Ensure hooks from GitHub (or whichever version control) feed into the scanning process for each commit.
-
Configure alerting and patch review workflows for developer/DevSecOps teams.
-
-
Governance and review
-
Set policy for human review of Aardvark’s proposed patches; ensure they align with coding standards, domain-specific safety / compliance constraints.
-
Monitor metrics: Mean Time To Patch (MTTP), number of vulnerabilities found pre-production vs post-deployment, false positive rate, developer acceptance.
-
-
Scale and expand
-
Once pilot results are positive, expand to all repositories; incorporate open-source dependencies scanning; integrate with supply-chain risk tools.
-
Use the agent’s output as part of compliance evidence (ISO 27001, NIST SP 800-53, etc), especially in complex engineering environments.
-
Risks and caveats
-
Over-reliance on automation: Even though Aardvark can propose patches, in high-stakes systems domain contextual knowledge remains critical (e.g., real-time loop control, redundancy logic, HSE implications).
-
Patch quality and context: Automated patches could introduce regressions, unintended side-effects, or violate architectural constraints. Human review and domain testing remain essential.
-
Data-sensitive systems: For industrial or critical infrastructure systems, you must ensure the scanning tool respects confidentiality and compliance (e.g., no exposure of proprietary code).
-
Integration lag and ramp-up: Embedding a new tool into workflow takes time — training, adjusting policies, tuning thresholds, aligning teams.
-
Organisational change management: Developer acceptance matters: if the tool produces too many low-value alerts, it will be ignored. Success depends on trust, relevance and minimal friction.
My verdict
From where I sit, Aardvark represents a meaningful advancement in software security tooling—especially relevant for engineering, industrial and enterprise systems where vulnerability risk translates not just to data loss but operational downtime, safety incidents, environmental exposure and supply-chain disruption. The ability to reason about code behaviour (rather than just mechanically flag patterns) and to validate exploitability and propose patches brings automation closer to how human security researchers operate.
That said, it is not a silver bullet. Organisations should approach its adoption in a structured way, with pilot programs, full human oversight, and integration into governance workflows. For teams I work with in the energy sector, this kind of tool could significantly reduce risk exposure in control-system software, IoT/OT stacks and supply-chain consumption of open source.
In summary: if you are part of a development organisation with high complexity, frequent commits, and significant risk exposure, I’d recommend factoring in tools like Aardvark into your security roadmap—especially as “shift-left” becomes vital in fast-moving digital operations.
FAQs
1. What is Aardvark in the context of OpenAI?
Aardvark is an autonomous security-researcher agent built by OpenAI, powered by the GPT-5 model, designed to continuously scan code repositories, build threat models, validate exploitability of vulnerabilities, and propose patches.
2. How does Aardvark differ from traditional vulnerability scanners?
Traditional scanners often rely on pattern matching, static code analysis or fuzzing. Aardvark adds reasoning about code semantics, behaviour and commit context, and includes a sandbox verification step plus patch generation.
3. What level of accuracy or performance has been reported for Aardvark?
In benchmark tests, Aardvark reportedly detected approximately 92% of known and synthetically introduced vulnerabilities in test repositories.
4. Can Aardvark integrate with our existing development workflow?
Yes — the tool is intended to integrate with source control platforms (e.g., GitHub) and continuous integration pipelines so it can monitor commits and produce actionable findings within the normal development workflow.
5. Is Aardvark generally available, or is it still in limited beta?
Aardvark is currently in private beta with select organisations and open-source projects; wider availability has not yet been fully announced.
Resource Center
These aren’t just blogs – they’re bite-sized strategies for navigating a fast-moving business world. So pour yourself a cup, settle in, and discover insights that could shape your next big move.
How the New AI-Assisted Skills Feature Empowers Developers to Architect Smarter Systems?
In today’s rapidly evolving digital landscape, developers face intense pressure to build complex applications faster while maintaining high standards of reliability, performance, and scalability. Traditional development methodologies are being [...]
AI-Assisted Development vs Vibe Coding: What Truly Scales in Production?
The rise of generative AI tools has transformed modern software development. From auto-completing functions to generating entire modules, AI-powered coding assistants have become part of daily workflows. Yet, not [...]
What OpenClaw Doesn’t Tell You: The Security Risks of AI with Full System Access
Over the last few months, autonomous AI agents have moved from experimental prototypes to mainstream productivity tools. Among them, OpenClaw has emerged as one of the most talked-about open-source [...]

